REvil Ransomware Uses DLL Sideloading
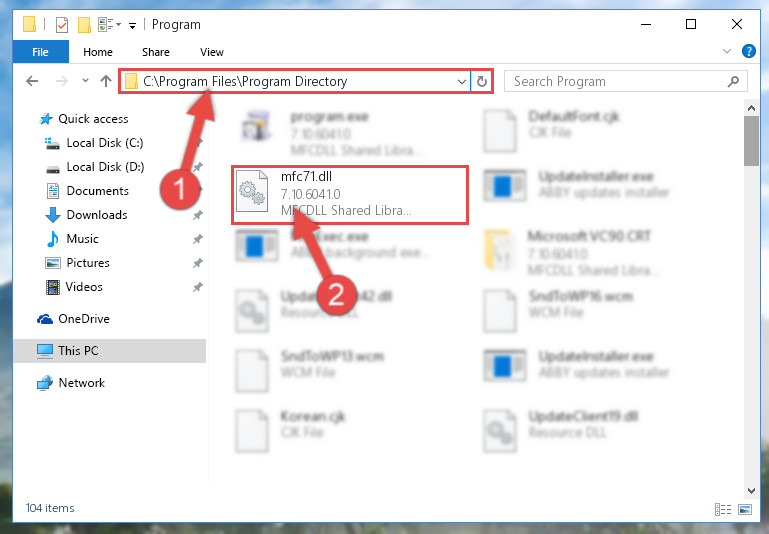
It then enables the program to detect and quarantine potential threats. Please press Start scan to start the threat search. A window with the installed programs will be immediately displayed.
- We have the same problem with the firewall in our company.
- Then I re-booted into safe mode as administrator, ran regedit and deleted all entries found with that file name.
- Ok so I just got done trying your method from above.
- It is recommended to run a scan before purchasing the full version of the software to make sure that the current version of the malware can be detected by SpyHunter.
Raspberry Robin also has been used to deploy the IdedID , malware loader Bumblebee, and the Truebot trojan. Scumbags also have ordered it to run LockBit ransomware and now Clop ransomware on hijacked machines, according to the Microsoft analysts. Fixes random crashing (after ~2 hunts) as of January 16th, including for other DLLs like ReShade and other DLL wrapper mods download api-ms-win-core-winrt-l1-1-0_dll. Sometimes these crashes would occur without any mods installed as well. Enterprises can use ExemptDomainFileTypePairsFromFileTypeDownloadWarnings to specify the filetypes that are allowed to download from specific sites without blocking.
This PC is TERRIFYING – Intel Extreme Tech Upgrade
First of all, it is worth understanding why a decrypt.dll file is missing and why decrypt.dll errors occur. DOWNIISSA uses the URLDownloadToFileA() API function to download the BLOB from the URL addresses and drop it as %TEMP%/$.tmp. Then it reads the file into allocated memory in the current process and deletes the downloaded temp file immediately. We confirmed that both URLs served the same binary data that was XORed with the one-byte XOR key stored at the end of the BLOB itself.
Static libraries are embedded into programs, which lead to duplicates among the multiple programs using them. DLL files are often used by programs that need to load various resources. For example, a program may need to load a DLL file in order to access a database.
Why do DLL files go missing?
We have the same problem with the firewall in our company. And I have tried the trick with renaming to ‘.bin’. Our firewall is checking the filecontent so renaming does not help.
Decrypting Password
Take the safe route and simply avoid downloading anything from these DLL download sites. Dll directly, which means using LoadLibrary() to load the . Dll into memory and then use GetProcAddress to get a function pointer . If your DLL function returns numeric data in a binary string format , it may return NULL values as a part of the data string. In such cases, passing arrays of short (8-bit) integers is most reliable.
You will most likely see the virus file there, maybe on top. If you disable it, it comes right back upon reboot. I have at least two dll’s in \system32\, both of which popped in there today after I was dumb and ran an exe. No, Firefox doesn’t require that DLL, something is modifying your Firefox after installation. Yes, but I don’t remember what the files were called. All I remember is that they were all “relevant knowledge” related.
Solicitar más información:
(si usted no quiere contactar con nosotros en línea, por favor rellena el siguiente formulario, después vamos a tomar la iniciativa para contactar con usted. Que estrictamente proteger su privacidad)
